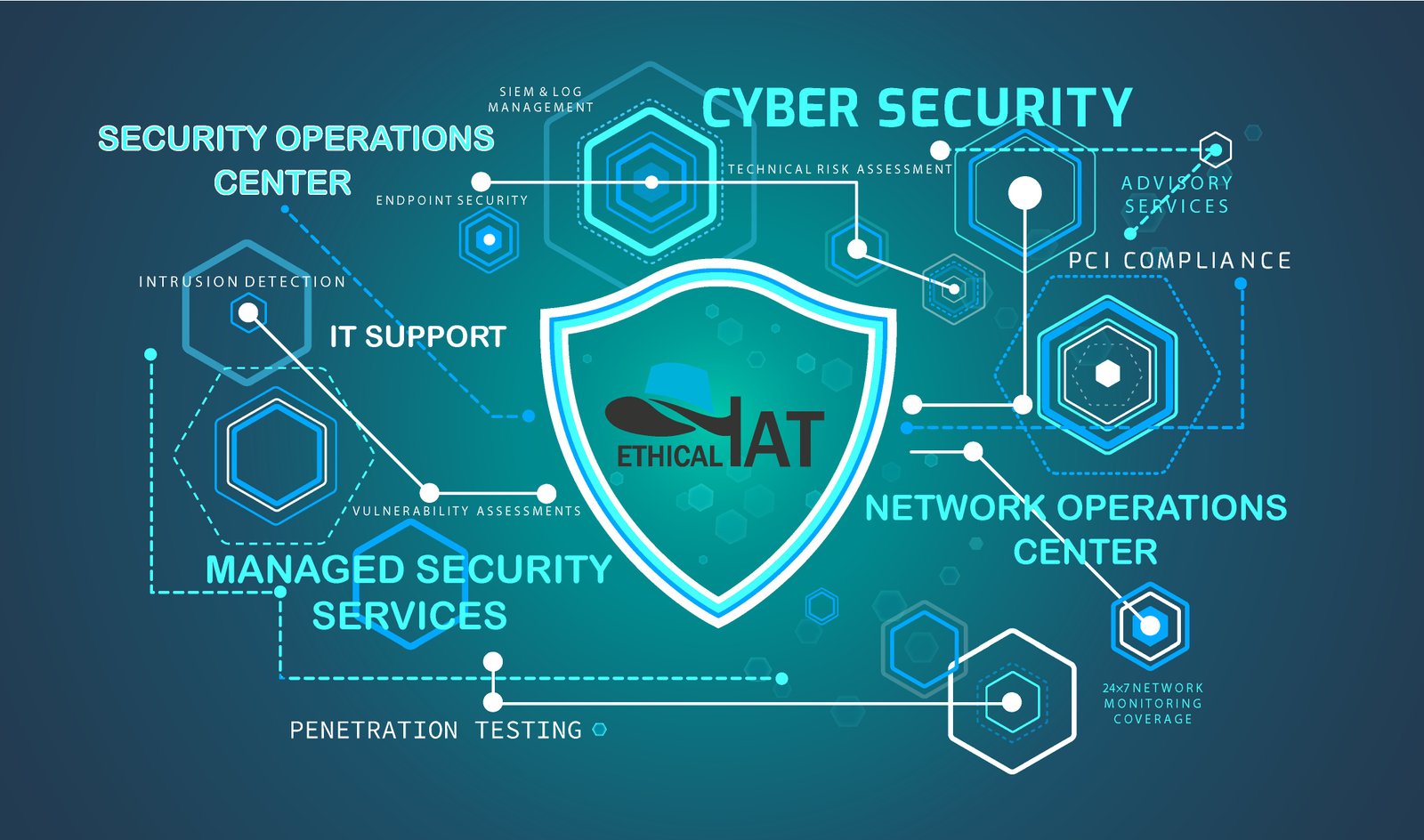
Cyber Security Management Services
We are providing the best Cyber Security and Antivirus protection solution service in Bangladesh. We help our customers to identify their security risks and define the measures to mitigate the risks by offering our competencies solution.
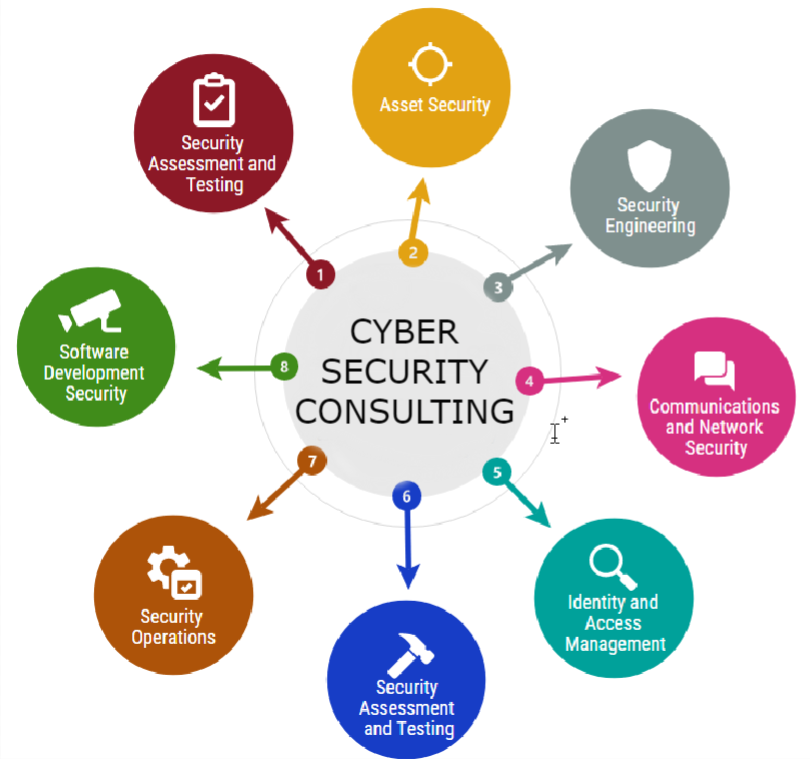
Cyber Security Services Protect Your Applications And Network
Cybersecurity services aim at assessing and improving the protection of applications and networks. Global IT Solution offers end-to-end information security services from IT security consulting to pentesting and enhancing cybersecurity posture to reduce risks and minimize consequences of cyberattacks.
We are a group of highly motivated security engineers who see online security challenges as opportunities to help diverse business models achieve their security objectives. Information security is not our career – it is our passion.
Managed Infrastructure Security
Your IT infrastructure needs a professionally managed security solution to ensure it smooth running and stay protected from cybersecurity threats. From a network to a server, all needs highly secured infrastructure to keep the data and systems protected from outside threats. CoreBitWeb offers managed infrastructure security for your business with proven security skills, expertise, and modern solutions.

Global IT Solution Are Providing Cybersecurity Services In The Following Areas:
- Vulnerability Assessment and Penetration Testing (VAPT).
- Managed Detection and Response (MDR).
- Identity and Access Management (IAM).
- Incident Response Planning and Management and Compliance and Risk Management
- Security Information and Event Management (SIEM.
- Firewall and Intrusion Detection/Prevention Systems (IDS/IPS).
- Data Loss Prevention (DLP) and Cloud Security
Enhancing Digital Safety: Comprehensive Guide to Cybersecurity Services
In today’s digitally-driven world, cybersecurity is not just a necessity—it's a critical component of any business strategy. With the increasing frequency and sophistication of cyber threats, organizations must prioritize their cybersecurity posture. This comprehensive guide delves into the essential cybersecurity services that can safeguard your digital assets and ensure business continuity.
Understanding Cybersecurity Services
Cybersecurity services encompass a range of solutions designed to protect information systems from cyber threats. These services are crucial for identifying vulnerabilities, preventing attacks, and responding to security incidents effectively.
Key Cybersecurity Services for Businesses
-
Vulnerability Assessment and Penetration Testing (VAPT)
- Vulnerability Assessment: This service involves scanning your systems to identify potential security weaknesses. Regular assessments can uncover vulnerabilities before cybercriminals exploit them.
- Penetration Testing: Simulating real-world attacks, penetration testing evaluates the robustness of your defenses. It helps in identifying security gaps and provides actionable insights to fortify your systems.
-
Security Information and Event Management (SIEM)
- Log Management: SIEM tools collect and analyze log data from various sources, providing a centralized view of your security posture.
- Real-time Monitoring: SIEM solutions offer real-time threat detection and alerting, enabling swift response to potential security incidents.
-
Managed Detection and Response (MDR)
- Threat Hunting: Proactively searching for threats within your network, MDR services enhance threat detection capabilities.
- Incident Response: When a threat is detected, MDR services provide immediate remediation actions to contain and mitigate the impact.
-
Firewall and Intrusion Detection/Prevention Systems (IDS/IPS)
- Firewall Management: Configuring and managing firewalls is crucial to control network traffic and prevent unauthorized access.
- IDS/IPS: These systems monitor network traffic for suspicious activities and automatically take action to block or alert on potential threats.
-
Endpoint Security
- Antivirus and Anti-malware: Protecting devices from malicious software is a fundamental aspect of endpoint security.
- Endpoint Detection and Response (EDR): EDR solutions continuously monitor endpoints to detect and respond to threats.
-
Identity and Access Management (IAM)
- User Authentication: Ensuring that only authorized users can access systems is critical for maintaining security.
- Access Control: IAM solutions manage permissions and roles, restricting access to sensitive data and systems.
-
Data Loss Prevention (DLP)
- Data Monitoring: DLP solutions monitor data in transit, at rest, and in use to prevent unauthorized access or transfer.
- Policy Enforcement: Enforcing security policies helps prevent data breaches and ensures compliance with regulatory requirements.
-
Cloud Security
- Cloud Security Posture Management (CSPM): CSPM tools assess cloud environments to ensure they adhere to security best practices.
- Cloud Access Security Brokers (CASB): CASBs provide a security enforcement layer between users and cloud service providers, protecting sensitive data.
-
Encryption Services
- Data Encryption: Encrypting sensitive data both in transit and at rest is essential for protecting it from unauthorized access.
- Public Key Infrastructure (PKI): PKI manages digital certificates and encryption keys, ensuring secure communication and data integrity.
-
Cybersecurity Training and Awareness
- Employee Training: Educating employees about cybersecurity best practices and common threats such as phishing is vital for maintaining security.
- Simulated Phishing Attacks: Regular simulations help test employees’ ability to recognize and respond to phishing attempts.
-
Incident Response Planning and Management
- Incident Response Planning: Developing and maintaining a comprehensive incident response plan ensures preparedness for security incidents.
- Forensics and Investigation: Analyzing security incidents helps understand the attack vector and prevents future breaches.
-
Compliance and Risk Management
- Compliance Audits: Regular audits ensure adherence to industry regulations and standards, such as GDPR and HIPAA.
- Risk Assessment: Identifying and mitigating risks to your information assets is crucial for maintaining a robust security posture.
Trusted By The World's Our Best Clients





































